Audit and Compliance Manager
ACM is an integrated and comprehensive tool set that enables core capabilities across the device life-cycle within the network: inventory, configuration, compliance and change management
Key Features
The adoption of ACM introduces business benefits including improvements in agility, efficiency,security, vendor and cost management. Also, it will accommodate the IoT growth, which willflood the network, by supporting device data consolidation, ensuring compliance, and automating deployment. ACM establishes its ROI in the form of reduced maintenance costs, reduced downtime costs, improved service delivery, and IT alignment with business goals.
- Manage up to 100,000 devices and configuration files
- Onboard devices and services
- Establish a reliable repository of configuration backups
- Visualize topology on map
- Support user-defined hierarchical compliance based on regions, customers, VPNs and other user-defined classes
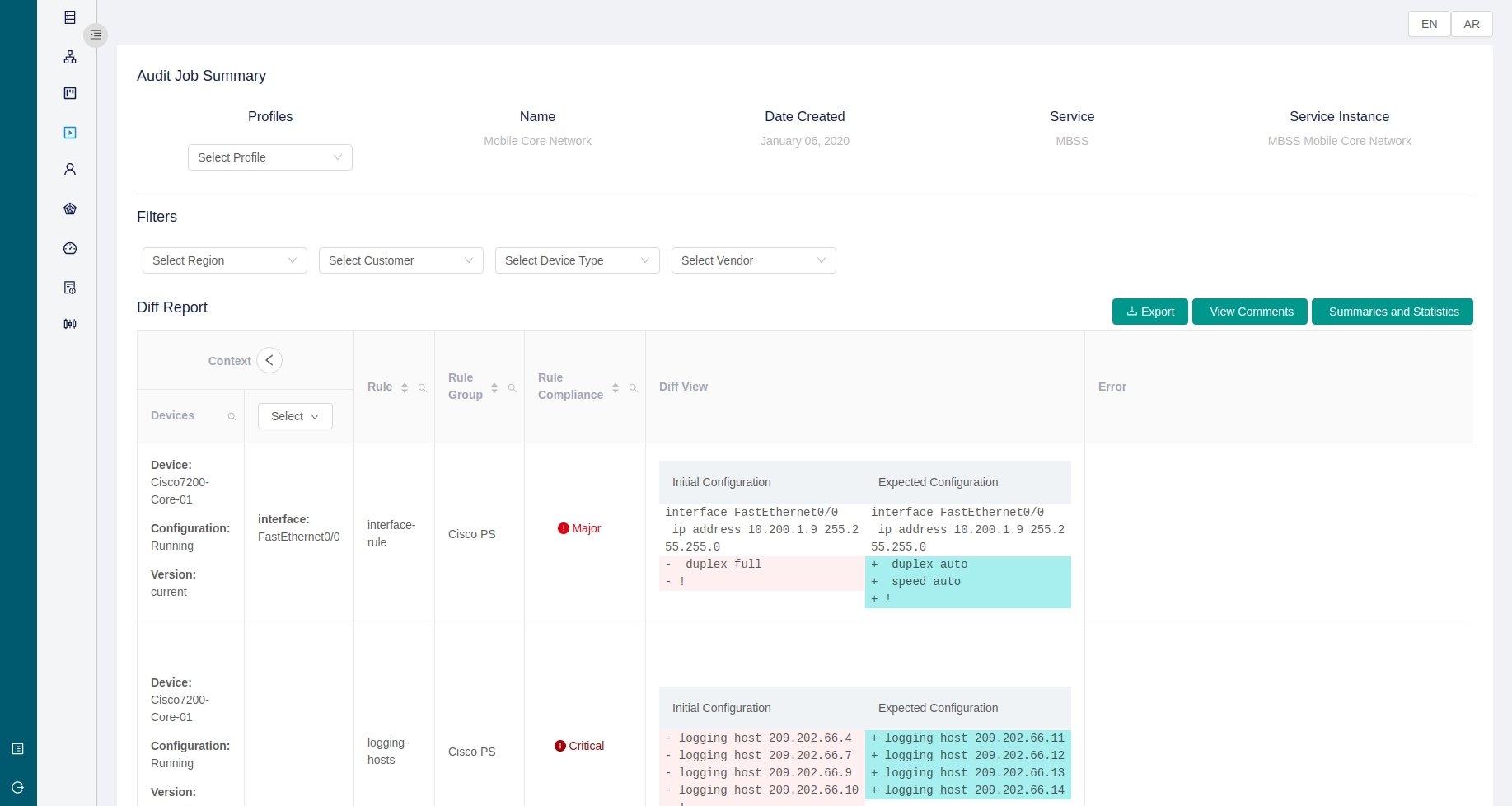
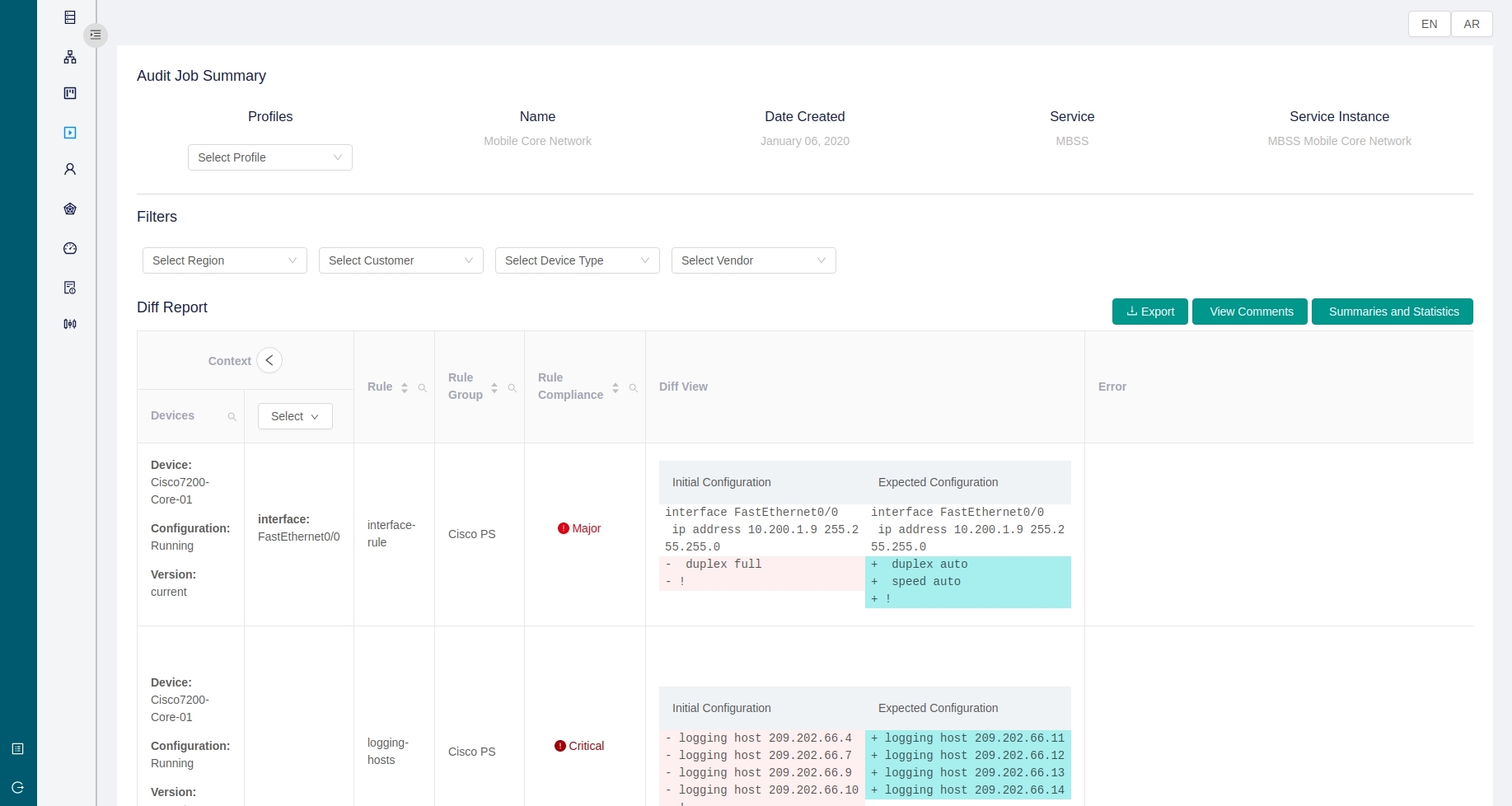
- Schedule compliance checks and generate DIFF reports, summaries, and scores
- Determine change impact and remediate devices
- Audit assets using RegEx matching and advanced python rules
Auditing your network has never been easier
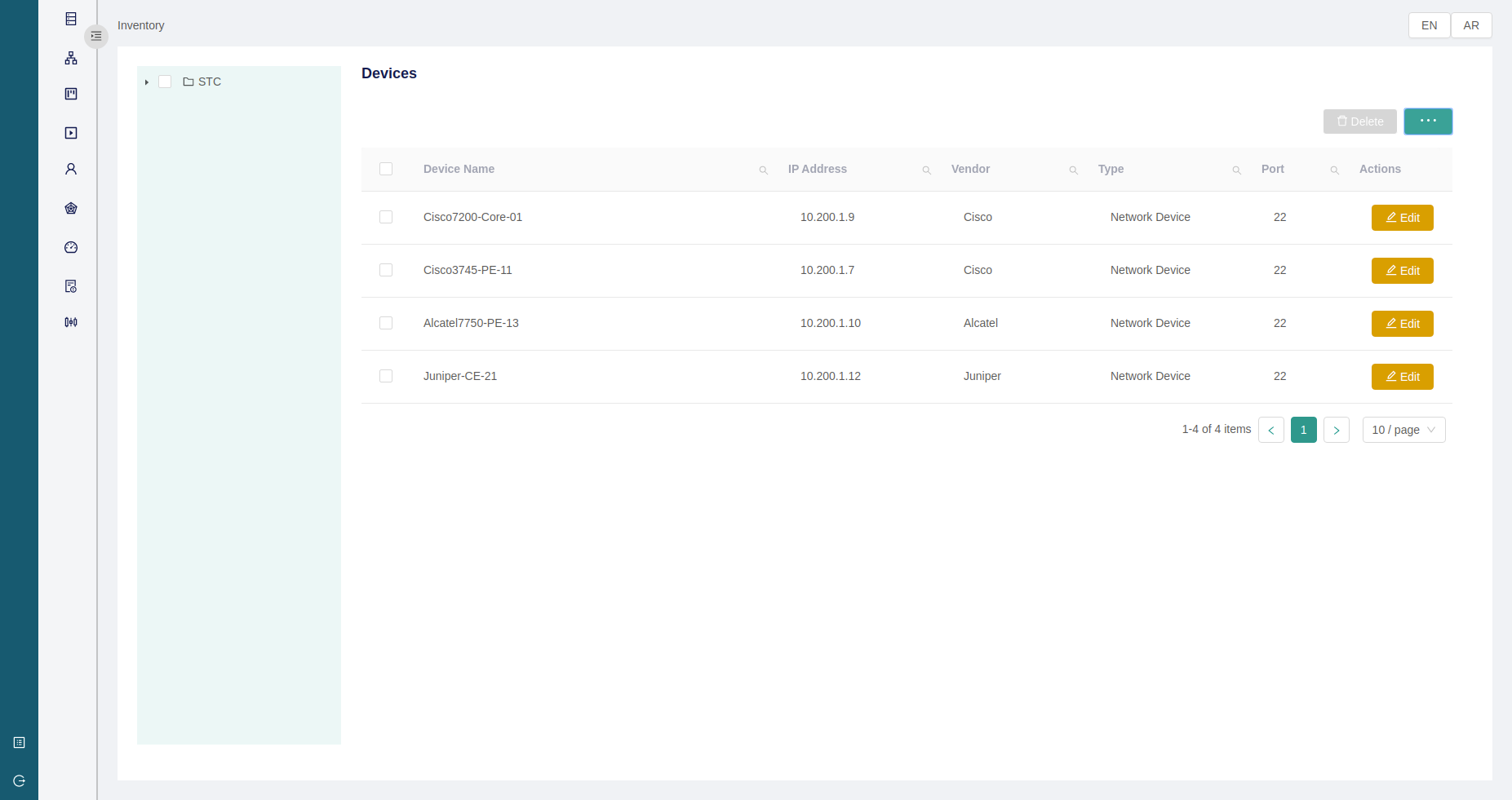
Inventory Management
The system provides an inventory manager as a centralized interface to view all devices being managed by the system including networking devices, orchestrators, controllers, VNFMs, and IoT devices.
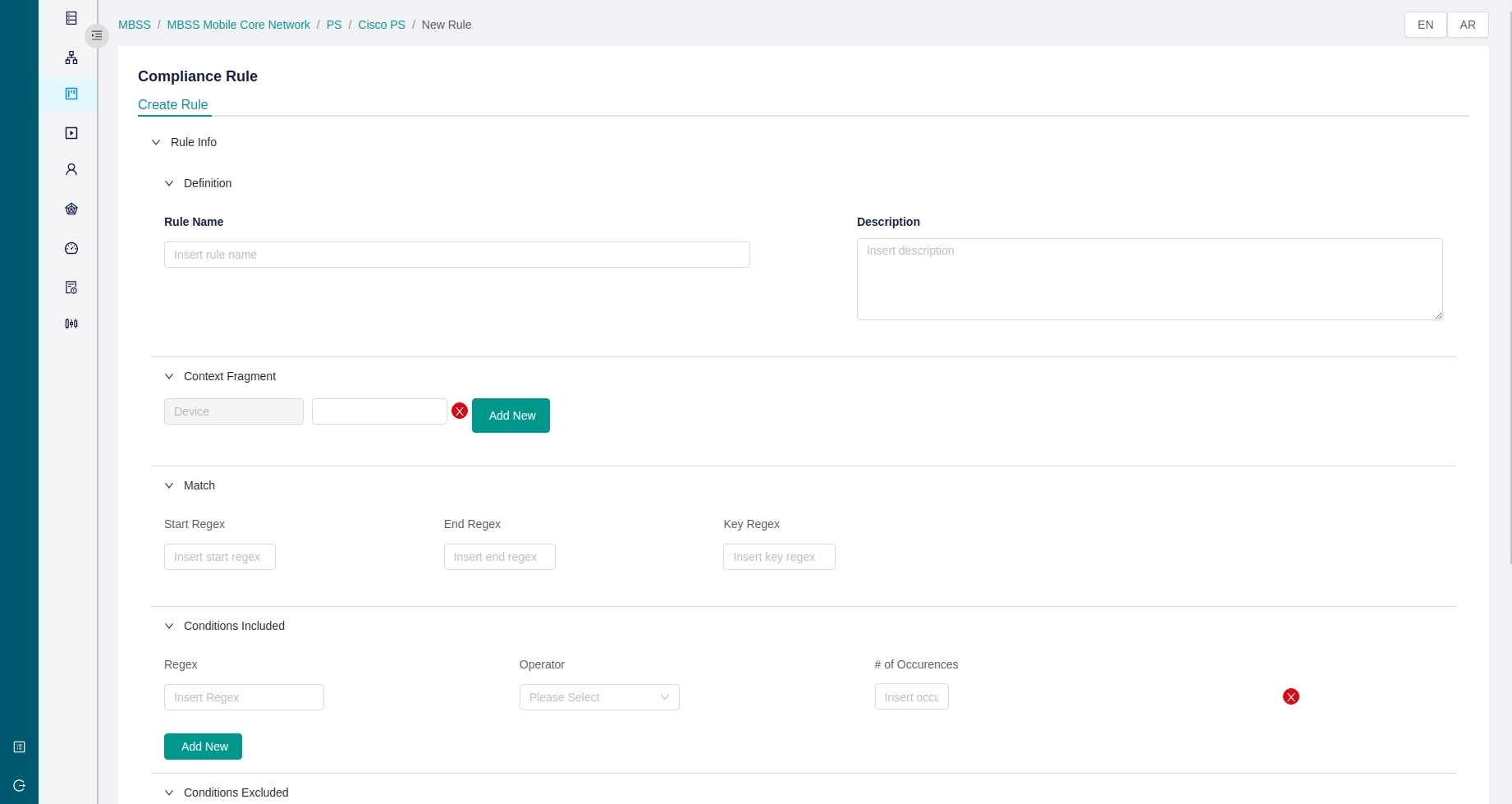
Configuration Management
ACM provides configuration management workflows to define intents using network service abstractions, create vendor-agnostic compliance rules and templates, and consolidate them into services, profiles, and rule groups.
Compliance Management
ACM provides the capability to audit the configurations of network devices to determine
their compliance with the configurations mandated by different user-defined services and golden templates.
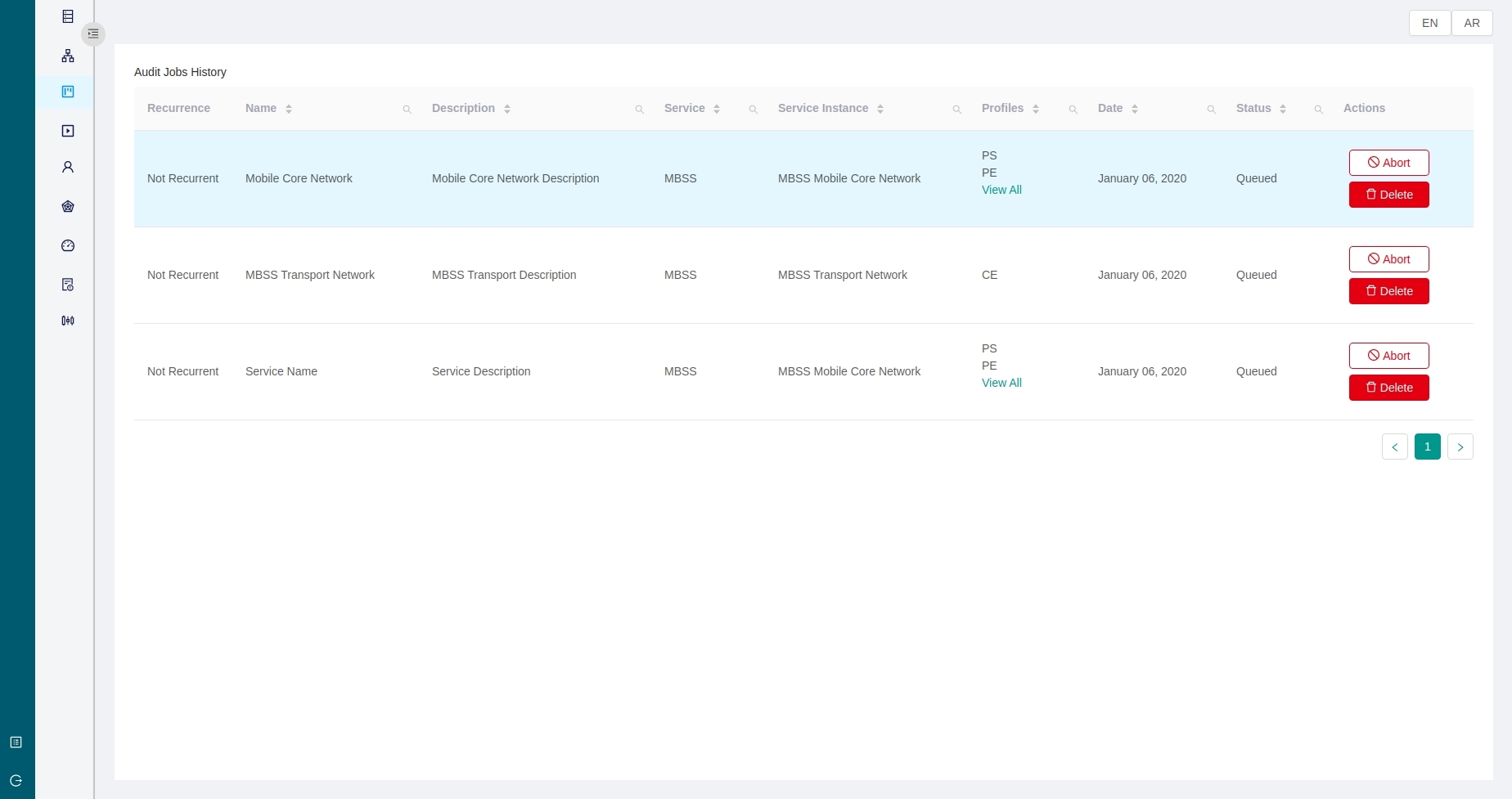
Change Management
ACM provides the ability to change the relevant device configurations such that they become compliant with the profiles and intents in accordance with the result of an audit.